VPS Hosting Security Best Practices and Measures
Security VPS Published on Date: October 11th 2023Well, having secure and protected VPS hosting is a must when saving your business data. VPS Hosting is a panacea and is renowned among businesses. Therefore, it’s vital to take security measures to protect your server.
This article will help you with the best VPS hosting security best practices for securing your online database.
What is VPS Hosting?
A VPS (virtual Private Server) is a virtualized server that runs independently. This VPS hosting maintains the balance where you can easily have control over a physical server. In VPS Hosting you have your own virtual server with relevant resources.
VPS Security Measures and Best Practices
1. Configure Firewall
Firewalls play a crucial role in securing your VPS by analyzing and handling incoming and outgoing traffic. VPS allows you to configure firewall rules, enabling you to restrict access to particular ports, services, and IP addresses.
Also, reduce the open ports numbers on your VPS by only allowing necessary services. Closing unused ported decreases the decrease the attack surface that will help to prevent unauthorized access. In addition, you can implement firewall filtering to scrutinizing network traffic and block malicious data packets.
2. Password Management
Passwords are your first shield to defend against attacks. Create strong, unique passwords for all services and accounts associated with your VPS. A strong username and password typically include a mix of Uppercase and lowercase numbers, letters, and special characters.
Also, many applications and services come with default usernames and passwords. Failing to change these defaults leaves your VPS vulnerable to attacks. Always change the default username and password credentials upon installation.
3. Regular Software Updates
Software vulnerabilities are a common target for threat attacks. Regularly update your server’s operating system, applications, and dependencies to deal with this risk. These updates often include patches that fix known security flaws.
VPS hosting Security measures also include implementing automatic updates whenever possible. This ensures that your VPS remains protected without requiring constant attention.
4. SSH Security
Secure Secure Shell (access) to your VPS hosting using key pair rather than relying solely on passwords. SSH keys provide a more robust authentication method, making it tough for attackers to gain access.
Secure Secure Shell (access) to your VPS hosting using key pair rather than relying solely on passwords. SSH keys provide a more robust authentication method, making it tough for attackers to gain access.
5. IP Whitelisting and Blacklisting
Whitelisting enables you to specify trusted IP addresses that can access your VPS. Conversely, IP blacklisting blocks specific IP addresses or ranges known for malicious activity.
6. Identifying and Blocking Malicious IPs
Use threat intelligence sources and tools to identify and block malicious IPs automatically. Therefore, frequently updating your IP backlists can help you to stay protected against malicious threats.
7. Virtual Private Network (VPN)
VPS encrypts data transferred between VPS and the local machine. This end-to-end encryption secures your data at the time of transition, making it hard to interrupt sensitive data.
Moreover, with VPS, you can gain secure remote access and ensure that all data traffic is protected and encrypted, especially when connecting over public networks.
8. Server Monitoring
On of the important measures among VPS hosting security tips is to deploy monitoring tools that track the performance and protection of your VPS. These tools can provide real-time insights into network traffic, resource utilization, and system health.
9. Setting up Alters for Unusual Activities
Configure alerts that notify you of unusual activities or deviations from normal behavior. This allows you to respond promptly to potential security incidents.
10. Log Management
– Collect and centralize server logs to facilitate analysis. Records can contain:
– Valuable information about system and security events.
– Helping you identify and respond to security events.
– Helping you identify and respond to security incidents.
11. Identifying Security Incidents from Logs
Regularly review the logo for signs of security incidents like unauthorized access attempts, unusual login patterns or system anomalies. Logs can act as a valuable resource for forensic analysis.
12. Disaster Recovery
Disaster recovery is about returning your VPS hosting environment to normal after a major incident or disaster. Establish and test disaster recovery plans that can help you recover data and systems efficiently.
13. Ensuring Data and System Recovery Processes
Document data recovery processes and system restoration procedures. Regularly test these processes to verify their effectiveness and minimize downtime in case of a disaster.
14. Compliance and Regulations
Compliance with industry-specific regulations is essential for businesses that handle sensitive information. Therefore, understand GDPR, HIPAA regulations to ensure VPS security. Also, different industries are subject to various regulation ensuring data protection and privacy.
Prioritize yourself with the appropriate security measures that may go with your business rules and regulations.
How to Ensure Compliance with Data Protection Laws?
To ensure VPS hosting security, make sure your security practices align with these laws, which may include access controls, data encryption, and data retention policies.
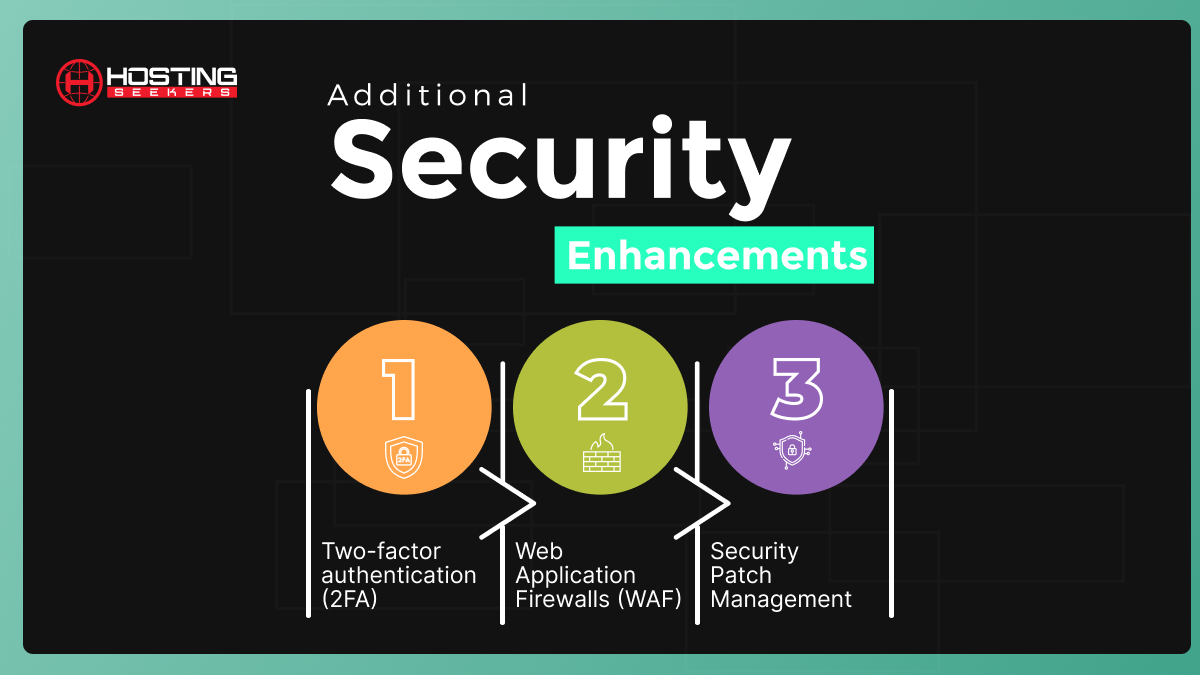
Additional Security Enhancements
While the foundational practices are critical, additional security enhancements can further fortify your VPS hosting environment. Here are some advanced security measures to consider:
Two-factor authentication (2FA)
Two-factor Authentication ensures security login by offering users to provide an additional verification beyond a password. This verification includes a code sent to their smartphones.
Web Application Firewalls (WAF)
Web Application firewalls are more protected and specialize security solution that secure your web apps from most common cyber-attacks.
Security Patch Management
This includes frequently updated your server along with your software, operating systems and application that are running on it. You can easily apply patches to check vulnerabilities.
Best Practices for VPS Hosting Providers
When selecting VPS hosting providers, your selection of VPS hosting providers plays a significant role. Here’s some steps when selecting a secure VPS hosting provider.
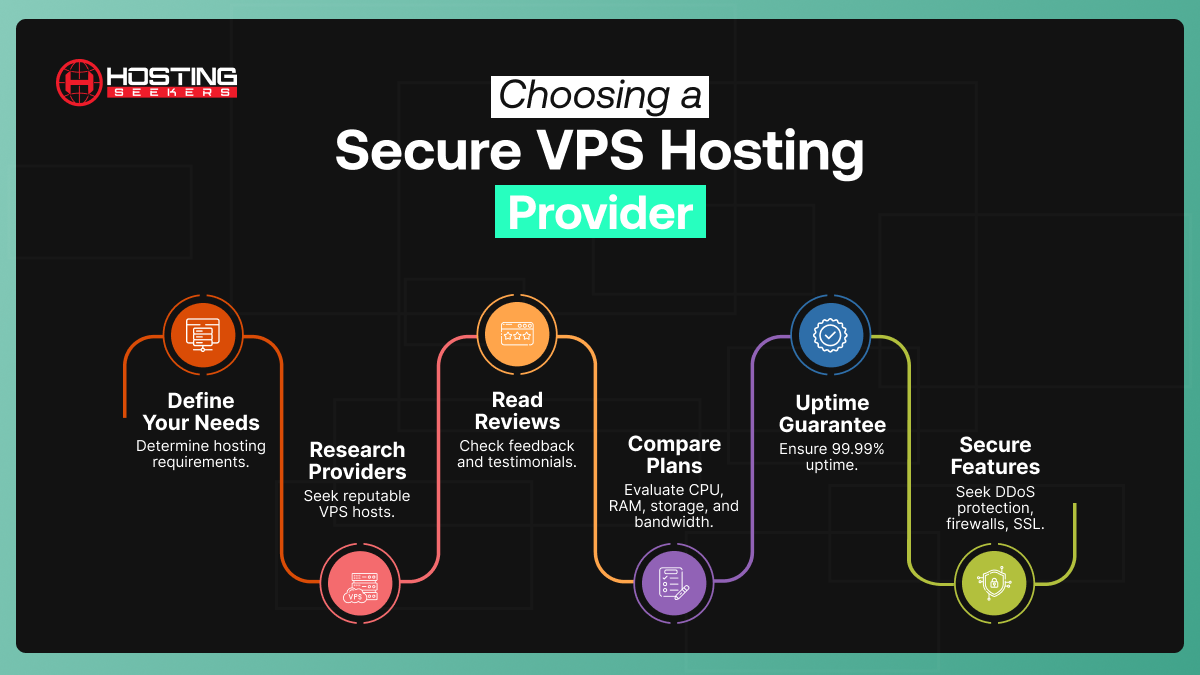
Choosing a Secure VPS Hosting Provider
- Step 1: Determine your Requirements: Define your needs and hosting requirements that include OS, resources, and scalability.
- Step 2: Analyze VPS hosting providers: Research for well-known VPS hosting providers. You can select the one which has good reviews.
- Step 3: Read Reviews: Reviews and testimonials play a crucial role. Therefore, you can read reviews and testimonials before opting for the VPS hosting provider.
- Step 4: Compare VPS hosting Plans: Consider features and compare plans also check for storage, CPU, RAM, bandwidth, and more.
- Step 5: Uptime Guarantee: When selecting VPS hosting plan, make sure your provider gains a high uptime guarantee.
Final Thoughts
By adhering to the best practices for securing a VPS, much can be done to improve virtual private server protection and minimize threats that may arise in the future. We must always remember that there is no endpoint when it comes to computer safety- knowing what new risks exist is equally important as applying these techniques. More so, defending your Virtual Private Server environment is no longer an option but a must, considering the rapid growth of online dangers. As such, selecting a reliable VPS Hosting security service would be ideal.
Frequently Asked Questions
Q1. What is the most crucial aspect of VPS hosting security?
Ans. While all security aspects are important, strong password management and regular software updates are fundamental for VPS hosting security.
Q2. How often should I back up my VPS data?
Ans. Regular data backups should be performed according to your data’s criticality, but a daily or weekly schedule is a good starting point.
Q3. What should I look for in a secure VPS hosting provider?
Ans. Look for providers with solid security features, including firewall protection, intrusion detection, and a commitment to regular software updates.
Q4. How can I comply with data protection regulations in my VPS hosting environment?
Ans. Please familiarize yourself with relevant regulations and ensure your VPS hosting practices meet their requirements. This may include data encryption, access controls, and data retention policies.
Q5. What are some basic security measures for VPS hosting?
Ans. Basic VPS security tips & measures include:
- Regularly updating your server’s operating system and software.
- Using strong passwords.
- Implementing a firewall to filter incoming and outgoing traffic.