What is DNS Attack and How to Prevent It?
Domains IT Published on Date: March 15th 2024DNS is an important factor of the internet. Well, A DNS attack is an attack that is centered on a network’s
Domain Name System. There are many DNS attack types but, in this article, we will focus on the DNS attacks and how to prevent them.
Also, this article will speak about the more common way that your DNS system may be in danger, how to lock it down, and how to mitigate and identify issues while securing DNS attack.
Table of Content
What is Domain Name System?
The DNS is a protocol that converts or translates human-friendly URL into IP addresses. We can say it’s a phonebook for the Internet.
DNS is compiled of several components: a recursive server, an authoritative name server, a TLD name server and DNS root Server. Attackers can utilize DNS to develop a control and command (C2), which would enable them to gain unauthorized access to a network and be able to exfiltrate data.
What is DNS Attack?
A DNS attack is when a hacker utilizes the data in the DNS services. The main aim of the attack is to make DNS service unavailable or corrupt the answers offered by the DNS server.
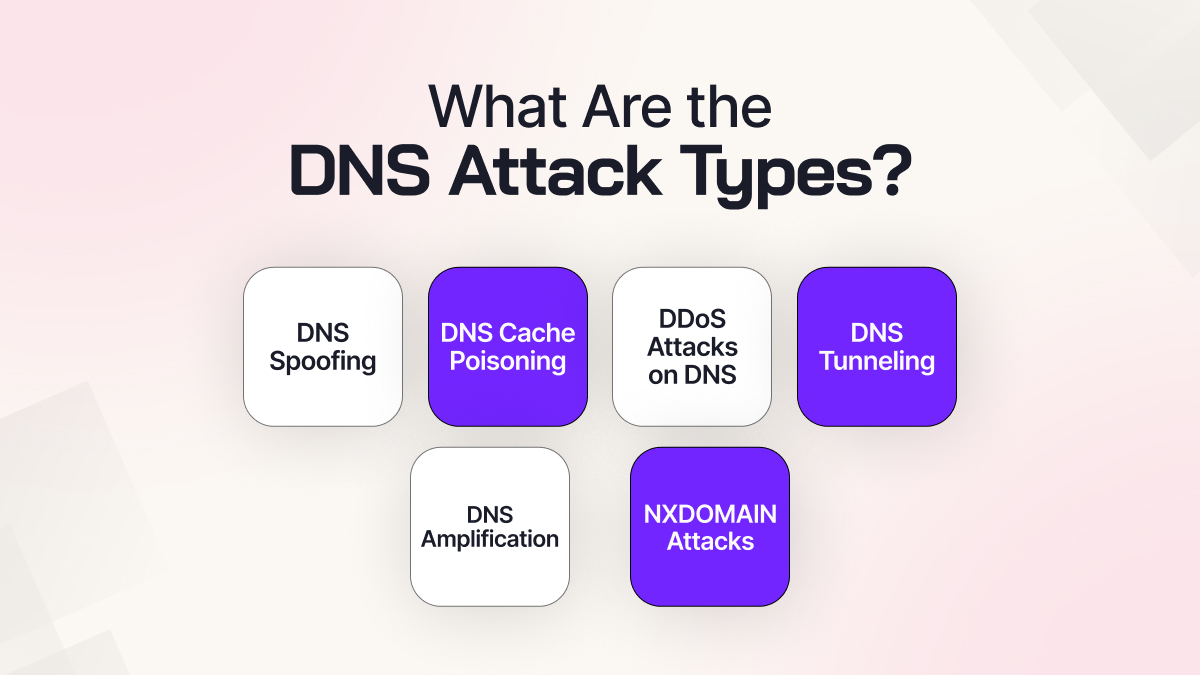
What Are the DNS Attack Types?
1. DNS Spoofing
The DNS spoofing, also known as DNS cache poisoning, involves attackers manipulating DNS responses to redirect users to fraudulent sites.
Dns spoofing attack can be achieved by injecting false data into DNS cache of a compromising or resolver authoritative DNS servers. Users may visit your sites, leading to phishing attack, data theft or other security compromises.
2. DNS Cache Poisoning
In this type of DNS Attack, malicious actors inject false information into the DNS cache, causing the DNS server to provide incorrect responses to the queries.
Uers mostly on the compromised DNS server that recieve incorrect IP addresses for domain names, leading to security risk.
3. DDoS Attacks on DNS
Distributed Denail of Service (DDoS) attacks flood DNS servers with an overwhelming request volume, rendering them unable to respond to legitimate queries.
This type of DDoS attack includes Denial of access, disruption of online services, potential financial losses for businesses. Including DDoS mitigation tools like traffic and firewalls filtering can help organizations mitigate and absorb the impact of DDoS attacks.
4. DNS Tunneling
DNS tunneling includes abbreviating non-DNS traffic within DNS requests, creating a covert communication channel that can detour traditional security measures.
Also, this attack on DNS facilitates unauthorized command and control communication, data exfiltration, or the establishment of covert channels for malicious activities.
Analyzing and monitoring DNS traffic for anomalies and implementing DNS filtering to block and detect tunneling attempts can help prevent unauthorized data transfer.
5. DNS Amplification
DNS amplification attacks perform Distributed Denial of Service (DDoS) on a target server. This includes exploitting open DNS servers that are publicly available, in order to overhwel, a target with DNS response traffic.
Typically, an attack starts with the threat actor sending a DNS lookup request to the open DNS server, spoofing the source address to become the target address.
6. NXDOMAIN Attacks
NXDOMAIN attacks flood a target with queries for non-existent domains, consuming computational resources and bandwidth.
Service degradation due to the excessive load on DNS servers, which potentially leads to downtime. Also, implementing rate limiting on DNS servers and employing traffic filtering can help mitigate the impact of NXDOMAIN attacks.
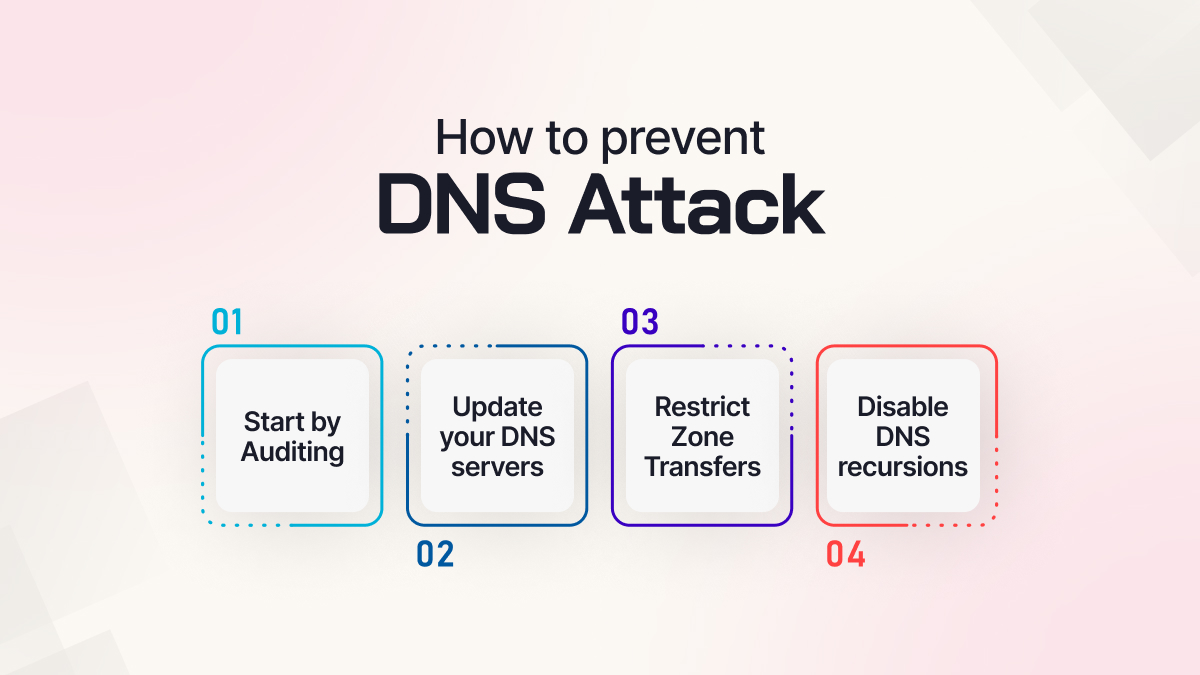
How to prevent DNS Attack?
1. Start by Auditing
The most vital thing you will have to review apart from the DNS server main configuration is your DNS zone.
With time, we also forget to test domain names or sub domains that sometimes-run outdated unrestricted areas or softwares vulnerable to attack or if an A record is highlighting an internal/reserved intranet area by mistake.
2. Update your DNS servers
Running your own name server provides you the ability to test, configure and try things that you may not be able to on private DNS servers like the ones your web hosting provider provides you or when your sign up for the Cloudflare account.
When you decide to run your own DNS servers, probably utilizing software like PowerDNS, BIND, NSD or Microsoft DNS, and as the the rest of the operating system software, so it’s vital to keep these packages updated in order to prevent service exploits targeting vulnerabilities or bugs.
3. Restrict Zone Transfers
A DNS zone transfer is just a copy of the DNS zone and while this technique is often utilized by slave name servers to query master DNS servers, sometimes attackers can try to perform a DNS zone transfer in order to have a better understanding your topology network.
Also, another vital factor that can be done to avoid such attacks on DNS is to restrict which DNS servers are allowed to perform a zone transfer, or at least limit the allowed IP addresses that make such requests.
4. Disable DNS recursions
DNS recursion is enabled default on most Bind servers. Also, it is enabled on major Linux distributions, and this can lead to serious security issues, like DNS poisoning attacks, and among others.
Also, when the DNS recursion is enabled on your server configuration, the DNS server allows recursive queries for other domains that are not real master zones that are located on the same name server, this simply allows third-party Hosts to query the name server they want.
Final Words
DNS attacks can have serious consequences but with the appropriate security measures in place, it is possible to overcome the risk of the DNS attack. By staying informed about the latest vulnerabilities and threats and implementing best practices for DNS security, you can help protect your organization from these types of attacks.
Frequently Asked Questions (FAQs)
1. What is DNS Attack?
A DNS (Domain Name System) attack is malicious attempt to disrupt the normal functioning of the DNS, that translates domain names into IP addresses.
Hackers attack vulnerabilities in the DNS infrastructure to redirect users to fraudulent websites, intercept sensitive information or disrupt services.
2. What are the different types of DNS Attacks?
-DNS Amplification
-DNS spoofing or DNS cache poisoning
-And DNS Tunneling
-DNS Hijacking.
3. How Does DNS Spoofing Work?
DNS spoofing attack incorporates the DNS cache of a DNS server or client to redirect domain name requests to malicious IP addresses.
Attackers achieve this by implementing false information into the DNS cache, leading users to fraudulent servers or websites which are under the attacker’s control.
4. What are the major consequences of a DNS Attack?
-Loss of DATA
-Financial Losses due to fraud or theft
-Damage to trust or reputation
-Legal and regulatory implications
5. How can I prevent DNS Attacks?
-Regularly update DNS patches and software to address known vulnerabilities.
-Implement DNSSEC (Domain Name System Security Extensions) to authenticate DNS responses and prevent DNS spoofing.
-Regularly update your DNS software and patches to address known vulnerabilities.
-Utilize reputable DNS service providers with built-in Secuity features.
-Monitor DNS traffic and analyze DNS logs for signs of malicious activity.
6. How does DNSSEC enhance DNS security?
DNSSEC utilizes cryptographic signs to verify whether the DNS response is authentic and preventing the integrity of DNS responses and ensuring that users are directed to legitimate websites.
7. Is it possible to recover from a DNS Attack?
Yes, organizations can recover from DNS attacks by restoring DNS configurations from backups, implementing security patches, and conducting thorough investigations to identify the root cause of the attack.