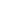Web Hosting Security Checklist 2025 | How to Secure Website?
Security Published on Date: October 29th 2021With each passing year, cyberattacks become more sophisticated, making it crucial for website owners to stay ahead of potential risks. To help you safeguard your online presence, we have shortlisted a web hosting security checklist to help you to secure your website.
Also, speaking about the market size, the global web hosting market size was valued at $57.46 billion in 2019, and is projected to reach $183.05 billion by 2027, growing at a CAGR of 15.2% from 2020 to 2027 (Source: alliedmarketresearch.com)
8 Steps to Make Sure that your Website is Secure in 2025
1. Avoid DDoS Assaults
Distributed Denial of Service (DDoS) attacks occur when a website is flooded with fake traffic, overwhelming its resources and preventing it from responding to legitimate user requests. Sending a large number of incoming messages, fake packets, or requests from multiple devices makes it challenging to block the attack source.
To protect against DDoS attacks, proxy servers can be employed to create a new access point and handle incoming traffic on behalf of the website. Among the various types of proxies available today, ISP proxies have gained popularity. ISP proxies combine the features of data center and residential proxies, offering a well-rounded solution.
ISP proxies are hosted in data centers but provide IP addresses from legitimate Internet Service Providers (ISPs). This combination allows them to offer both stability and authenticity. During a DDoS attack, ISP proxies can be useful in mitigating the impact by increasing bandwidth to handle sudden traffic spikes.
2. Protection Against Brute Force Attacks
A Brute Force Attack is a hacking technique where the attacker employs a trial-and-error approach to guess your password. Hackers utilize computers and software to try numerous combinations until they find the correct one systematically. Despite being an older method, hackers still employ brute force attacks effectively.
Your website hosting company should implement safety measures to thwart brute-force attacks. Additionally, you can take extra precautions to enhance your protection. These safeguards include regularly changing passwords and using strong, complex ones each time. Enabling two-factor authentication (2FA) and employing firewalls add a layer of security to your system.
3. Shield Against XSS Cross-Site Scripting
XSS, also known as cross-site scripting, involves an attacker injecting malicious code into an unsuspecting website. Once users visit the compromised site, their browsers execute the code, enabling the hacker to gain access to the information exchanged during that session. Such attacks take advantage of various vulnerabilities present in websites, making it challenging to shield them effectively.
All types of web hosting providers, including those using Amazon Web Services (AWS), implement countermeasures to safeguard their users from these malicious attacks. AWS, as a web hosting provider, offers robust security measures to protect against XSS and other vulnerabilities, ensuring a safer online environment for website owners and visitors alike.
4. Prevent SQL Injections
To safeguard against SQL injections, it’s crucial to be aware of potential hacking attempts that may compromise your database. Attackers exploit vulnerabilities by injecting malicious SQL codes through input fields, granting them unauthorized access to edit or delete website data. Detecting authentic and harmful queries can be challenging, making it a serious threat.
Choosing web hosting services on AWS can be beneficial in preventing SQL attacks. Verifying if your hosting provider implements effective countermeasures can significantly reduce the risk of encountering such troubles.
5. Backup Your Data
Data is an indispensable necessity for any business, and experiencing data loss can result in catastrophic consequences that nobody wants to face. It is crucial to have backup data readily available, as it can rescue you from potential system failures or malicious attacks that may cause data loss.
Web hosting services should offer cloud storage options where you can securely upload your data. By using dependable cloud storage, your data remains safeguarded and easily accessible from any location.
6. Prevent Spam
Website crawlers evaluate various parameters to rank websites, and the comment section is one of them. If your website is overwhelmed with spam comments, it can negatively affect your ranking. To prevent this, consider choosing a hosting service that provides spam detection. Identifying and removing spam early on will help maintain your website’s credibility and improve its ranking.
7. Secure an SSL Certificate
The lock symbol or HTTPS at the beginning of a URL indicates that a website is secure. In simple terms, it means that the website has an SSL certificate, which enables it to use HTTPS for security purposes. The switch from HTTP to HTTPS can have a significant impact on your website’s performance.
For end-users, seeing the lock symbol instills confidence while browsing your site. It assures them that any information they share is encrypted and less likely to be intercepted by malicious entities. People visiting your site tend to check for this security symbol before providing sensitive information.
8. ISO 27018 Compliance
ISO 27018 is a set of rules designed to safeguard consumer data from unauthorized access. It ensures that customers are aware of the location of their data at all times and that this data is only shared when legally required. Companies cannot use this data for targeted advertising without the customer’s explicit consent.
To ensure the utmost protection for your data, your web hosting provider must adhere to ISO 27018. AWS also offers compliance with these protocols.
Conclusion for Web Hosting Security Checklist
Web Hosting Security Checklist for 2025 provides essential guidelines to ensure the utmost security for your website. By adhering to these recommendations, you can effectively safeguard your website against potential threats and vulnerabilities. Protecting your website is of utmost importance, and by following the latest security measures, you can create a robust defense against cyberattacks and maintain a safe online environment for your users.
Author Bio
Daniel Martin loves building winning content teams. Over the past few years, he has built high-performance teams that have produced engaging content enjoyed by millions of users. After working in the Aviation industry for 9 years, today Dani applies his international team-building experience in LinkDoctor to assist in solving his client’s challenges. Dani also enjoys photography and playing the carrom board.